|
DECRYPT FACILITY FOR OTP TRAFFIC
An
historical and
generic overview of One Time Pad message deployment may be found
here:
Here is Dirk Rijmenants' complete technical manual for using contemporary One Time Pad encryption: https://www.ciphermachinesandcryptology.com/en/onetimepad.htm Dirk Rijmenants describes in great detail the professional spies’ highly disciplined approach with the best trade craft in mind. When used correctly to the last detail, any OTP-encyphered message text is uncrackable. However, when deployed in an amateur radio environment, such extreme security as Dirk describes is not achievable due to the need for transparency, i.e. to make key groups public. This requirement is to permit the ‘authorities’ to decrypt such traffic in order to allay any suspicion that something treasonous, or contrary to the principles of amateur radio is being transmitted. That’s a small price to pay for being able to participate in an historically accurate activity available only to those willing to put in almost the same degree of personal effort and dedication as military-grade radio operators of WW1 and WW2, such as were associated with SOE, OSS, MI5, La Résistance et al, the Wehrmacht, Luftwaffe and Kriegsmarine, right up to today’s CIA, FSB, DGSE, SWW, and of course myiads of other foreign security agents who listen(ed) to their respective country’s number stations transmitting instructions. Enough romanticising and down to business ... So long as two or more participants agree on a common method of encryption, i.e. are using the same resources, they may exchange Enigma or OTP traffic by telephone, echolink, email, or in fact by any medium in which transparency is not an issue. Transparency is however vital to avoid any unpleasant consequences when using amateur radio live on- air. Transparency is achieved by providing an easily accessible decryption facility appropriate to the encryption type. Annunciation of such facility must be an integral part of the item of traffic, e.g. a URL appropriate to the encryption method is always provided in an OPNOTE. OPNOTES are outside the message text and are not included in the CHECK field. Where OTP is concerned, there are hundreds of possible predetermined combinations. To keep it simple only four options are used on the SAS Net, each instantly recognizable: 1. Manual method uses Conversion Chart No. 03086, where the message text is sent in 5-digit groups; 2. Assisted method using Dirk Rijmenants' CT-46 conversion table also configured in 5-digit groups; 3.
Manual method 1 followed by Stephen ZL1ANY's
Python error detection utility, in which the message text 4.
Assisted method 2 followed by Stephen ZL1ANY's
Python error detection utility, in which the message text
|
|
How to Decrypt a simple OTP-encrypted Message
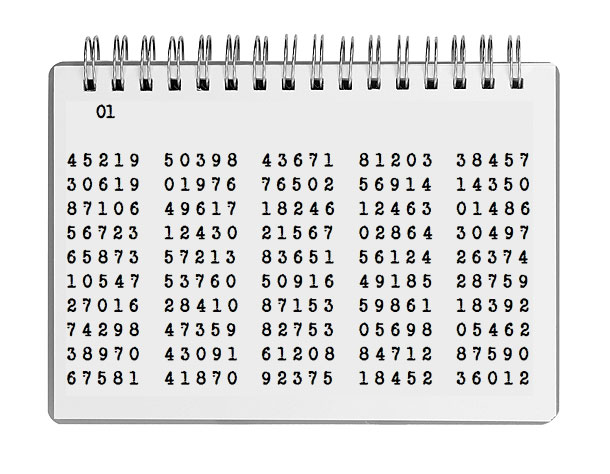
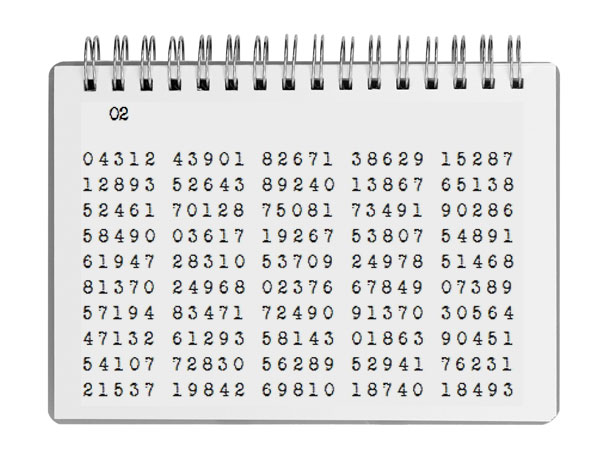
Every QTC encrypted using an OTP will end with an OPNOTE giving a URL which points to this decryption facility. We’re not trying to hide anything. 1. Look at the date in the preamble, is it an even or an odd day? The answer determines which key page to use. To keep it simple, there are only two, non-disposable key pages. These key pages, in bare the format shown may be used for message texts up to 245 characters, however by scrolling and reusing the groups, any length message can be encrypted. The first group selected for the key sequence remains in clear and is called the key indicator. The key indicator is not used to encrypt the message, but is prefixed to the encrypted message text. If the key indicator cannot be found on either page, the message was not encrypted from this OTP. When decrypting, the first group in the message text is extracted in clear to reference the start point of the key page sequence.
Both OTP code pages may be downloaded as text files for easy copy and paste.
Manual Method 1.
|
|
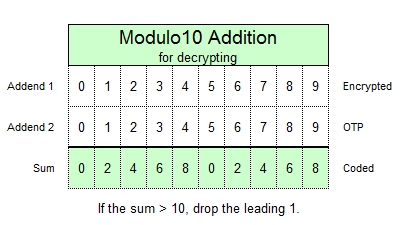
Write the one-time pad digits beneath the encrypted text and modulo10 add them, digit by digit, from left to right, the in clear key indicator is in RED: Encrypted:
68496 32579 24623 65030
96188 42672 00212 01749 61591 After decryption, the resulting plain-code number string is converted into plaintext using one of these two conversion charts, depending which was used to convert clear text to the number string originally.
|
|
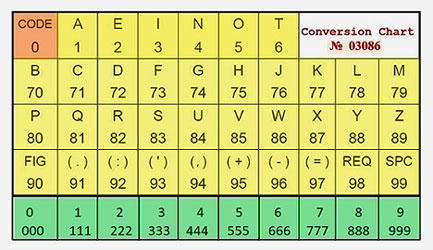
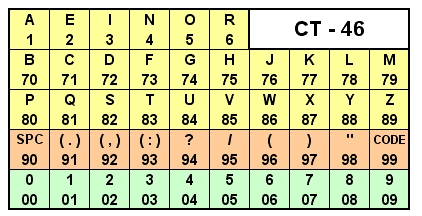
For this example we're using the using the upper conversion chart, Nr 03086 ... 1. When the first or next digit in the number string is between 1 and 6 inclusive, it represents a single-digit value. 2. When the first or next digit is 7, 8 or 9, it represents a double-digit value and the following digit will be appended to make a double-digit value between 70 and 99 inclusive. 3. If the first or next digit is a single 0 (CODE zero), it will be followed by a three-digit code that represents a word or expression from the optional code book. Obviously both sender and receiver must be in possession of a copy of the same version code book. 4. When a group of three of the same digit is encountered, they represent one same value digit. 5. Our message can now be converted into text using the conversion chart thus: 79 2 2 6 3 4 74
99 1 6 90 111 444 90 80 79 99 3 4 99
4 88 91 91
When using the Python command line window, text
cannot be cut/copy/paste by mouse alone.
|
|
Method 2. Decrypt a Python-Assisted, Error-Detecting, OTP-encrypted Message This type of QTC is distinguishable from the simple number-station style traffic by its 6-letter alphabetic groups. 1. Download the zipped CT-46 encrypt/decrypt utility. Change the filename extension from .jpg to .zip and install. 2. Download Python from https://www.python.org/downloads/release/python-3122/ and install.
3. .exe-type files such as Python .py files may be
seen as a security threat by some browsers and will not be able to
be downloaded. For this reason the Python files have
their extensions changed .jpg After downloading, each file
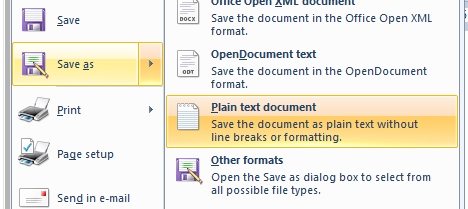
must have its extension changed back from .jpg to .py To convert the 6-letter groups to 5-digit groups, and concurrently check that each group has been received correctly, save the received 6-letter groups to a plain-text file, most easily achieved using WordPad.
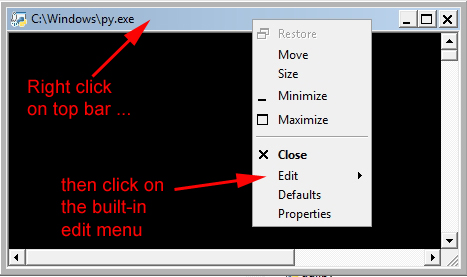
Invoke the Python file rf.py whereupon it
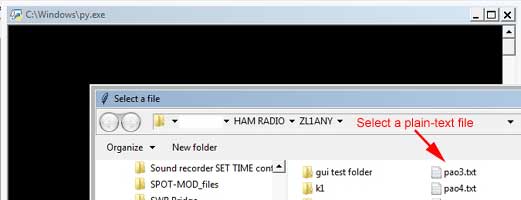
will open a file explorer window. Click on the saved plain-text
file.
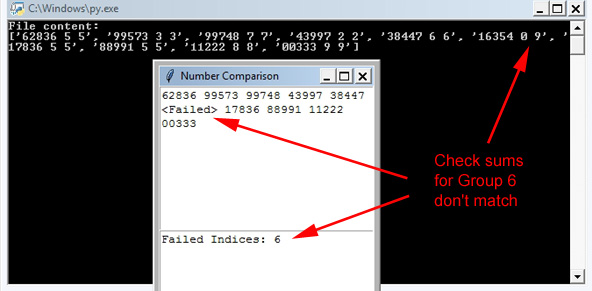
If a receive error has occurred the faulty group is identified:
If no errors are reported, save the
entire data string to another plain-text file and delete everything
other than the 5-digit groups. Error detection is complete and the
numbers string is now the same as if it had originated from a numbers station.
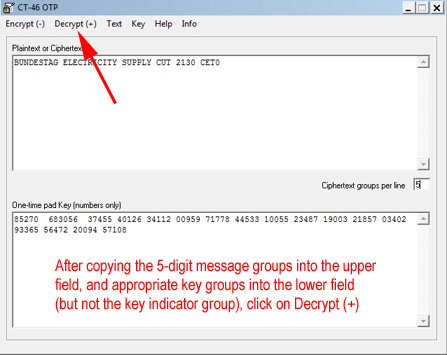
If errors have been reported, request a resend of only the error-affected groups, correct the first plain-text file which contains the original 6-letter groups and repeat the process with rf.py until no errors are reported. Once the 5-digit groups are error free, save the data stream to another plain-text file and delete everything other than the 5-digit groups. Save again. Error detection is complete and the numbers string is the same as that from a numbers station. Invoke the CT-46 application:
The message is now showing in clear Caution: This page and its associated encryption instruction page may be updated as various software is replaced due to improvements - or OTPs are changed. Always refresh these pages before using them to ensure send and receive stations are using identical protocols and data, in the electronic equivalent of physically delivering replacement OTPs and conversion charts to agents in the field.
|
|
|