|
|
How to
Manually Decrypt
a One Time Pad
Message using a No.03086 Conversion Table |
| 1. Open a new text file in which
to save every step, then archive it when your
message has been
fully decrypted. That will
make troubleshooting less tedious should it not work
correctly
the first time. |
| |
|
2. Copy the entire received
encrypted QTC and save it to the new text file.
Keep the text file open. |
| |
|
3. Check the date in the preamble;
use this day number to select the correct key page.
The key pages may be
downloaded for instant reference. No need to
destroy them after use as
would normally be the case with OTP key pages in security-critical
environments.
For amateur radio deployment we reuse them every month. |
| |
|
4. The first 5-digit group in the
message field is the key locator. It can be
found in the appropriately dated key page using a normal <Ctrl-F> search.
Having found the key locator, copy and paste to
your text file at least as many key groups AFTER the key
group as there are
5-digit groups in the received message.
If the key locator is close to the bottom of
the page, it will likely be necessary to copy all the
groups below it, plus more groups working down from the
top. Save all these groups to your text file, but
don't include the key locator group since it has already fulfilled
its purpose to identify where the key groups begin. |
| |
|
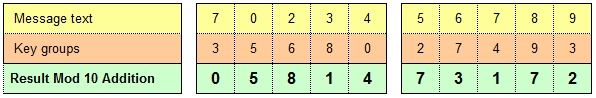
5. Write the 5-digit message groups a cross
a multicolumn sheet of paper, then arrange the 5-digit
key groups beneath. Perform Modulo-10
addition on each 2-digit vertical column.
That means there is nothing to carry to the next-left
column when the sum of any column is greater than 10.
|
|
 |
| |
| |
|
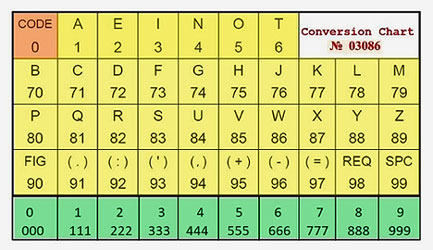
6.
Now the resulting 5-digit groups are ready to be
converted from code to plain text using a prescribed
conversion table, in this case it is No. 30386
shown below.
This is conversion table No. 03086 was used
to originally code the message. Each
5-letter group in the revealed text is not in isolation.
There will be many instances where a character code
spans two groups. e.g. 'G'
may be represented by the last digit, a 7 in one group,
and the first digit, a 4 from the following group.
 |
| |
|
7.
This final move may or may not be necessary.
If the encrypting operator made correct use of the space code 99,
inserting and
deleting spaces to form the text into readable words
may not be necessary. |
| |
| |
| |
| |
Listeners are invited to join in by copying
encrypted traffic regardless
of the addressee, decrypt it and send the result by email to:
Guaranteed acknowledgement. If no reply within
48 hours please resend.
Before transmitting any
encrypted messages on the SAS Net,
please become familiar with the
Rules of Engagement
to ensure compliance.
Messages in clear are not covered by the Rules of Engagement.
Here's
an opportunity to put your CW skills to serious use through
innovation, challenges,
encryption and plain-text QTCs.
Between weekly nets, calling frequencies are
3.567 MHz and 7.0257MHz,
for testing and encryption experimentation purpose.
Please
send your formal, encrypted QTCs
via the Thursday SAS Net
so that
everyone has the opportunity to participate.
A resource providing many encryption options,
not all are suitable for CW:
https://cryptii.com/
It runs on your browser Java platform and does
not need installation ... try it, it's clever, but
understand
you are undertaking an academic exercise without experiencing a
hands-on machine.
Experimentation with
diverse encryption methods is welcome, so long as a
URL
pointing to an ad hoc decryption facility is made
available, either via
an OPNOTE
giving a shortened URL (recommended) or verbosely (not recommended).
|


